Overview
As with many computer related issues, we have to balance two competing interests:
- Make it as easy as possible for our donors to give us money online
- Stop credit card fraudsters from abusing our online donation tools
Most of us our familiar with the first interest, but what about the second?
Turns out, there is a huge black market in stolen credit card numbers. Every time you hear about a major corporation making a stupid mistake resulting in thousands or millions of credit cards being stolen, those card numbers go straight to the black market to be sold. However, before selling them some of the more "ethical" criminals need to know which credit card still actually work.
That's where your Powerbase contribution page comes in. The criminals use automated programs to submit credit card contributions over and over again to see which ones work and which ones don't.
Please note: If you are using the Stripe payment processor, these mitigations will not work. Please scroll to the "Handling Credit Card testers" section on our configuring stripe page.
How to stop them
We try to interrupt this process using a few methods that are on by default:
The fraudsters often pick random amounts that don't have an even dollar total (e.g. $20.43). So, if we detect an uneven dollar amount, we reject it.
In addition, we keep track of which computer is submitting contribution requests and if we notice that the same computer is submitting more than 5 requests during a 2 hour period, we stop them.
And, we detect if a contribution page is submitted less than 5 seconds after it was loaded and block the submission if it was.
These steps generally work pretty well.
Yeah, they seem to be working too well! How do I turn them off?
Unfortunately, sometimes our attempts to stop fraudsters are triggered by people just trying to make a donation.
The most common case is if you have a fund raiser and you have a public tablet computer available for people at the party to make their own contribution. Since everyone is sharing the same computer, the contributions will all come from the same IP address and after four have been made in the same hour, you will be blocked.
If your users are experiencing this problem, they may see errors like the ones below:
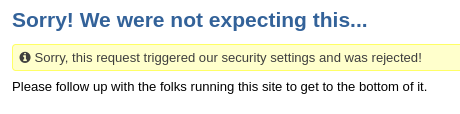
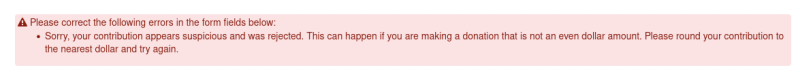
To address this problem, we have made it possible for you to turn on and off this feature - so you can disable it before your fundraiser and enable it after words.
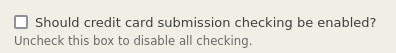
To turn it off, click Administer -> System Settings -> Validate Settings and uncheck the box to disable validation:
But other times, they just aren't enough
If our default methods are not enough, we have more tricks up our sleeves.
Set the Minimum Amount
An effective method is to modify your contribution pages to either disable the ability for donors to contribute their own amount OR if you do enable this feature, set a minimum contribution amount that is $10 or more (most fraudsters don't want to test with a high amount because that would increase the odds of the credit card owner to see the charge and cancel their card).
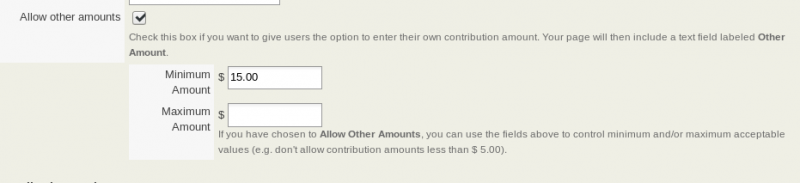
If your contribution page uses a price set, then you'll need to edit the price set and set the minimum amount there. First, go to the Price set listings page via Contributions -> Manage Price Sets. Then, click the "more" or "..." link and choose "Settings":
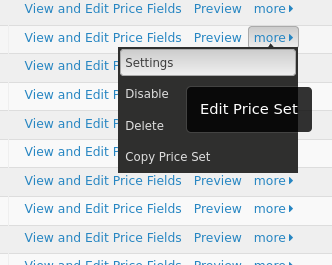
Then, change the "Minimum Amount" field.
Add re-captcha
You can add a re-captcha screen to your contribution page by following our from protection instructions.
Getting more aggressive
Sometimes you need to get even more aggressive, if only for a temporary amount of time.
You can do that via the Validate settings page: Administer -> System Settings -> Validate Settings:
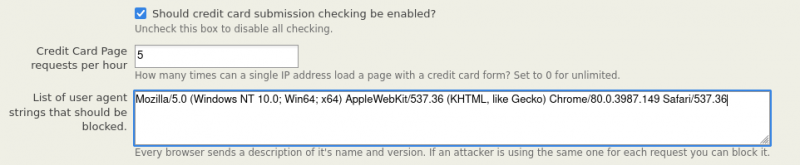
- Credit Card Page Request Per Hour - By default we only allow 5 credit card page submissions every 2 hours. But, some attackers are sneaky and they request the contribution page, extract the session codes they need and then submit directly to the back end, evading our submission checks. By entering a number in this field, we limit how many times an IP can access the contribution page itself in a single hour.
- List of User Agent Strings - When very desperate we can block a user agent string. Sometimes if an attacker is careless, they use the same user agent string over and over again. By blocking it, we can stop them immediately. We also run the risk of blocking other users with the same string, so it's a very blunt tool that should only be used sparingly. A string that has been known to be used by attackers in the past is: "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.149 Safari/537.36"
